Managed Apple IDs | Kandji
Managed Apple IDs are Apple ID accounts that your organization owns, controls, and assigns to users. Like any Apple ID, Managed Apple IDs can be used to sign in to devices and services.
Organizational ownership means the organization is responsible for things like password resets and role-based administration for those IDs, as well as defining how they will be created and distributed to users.
Nội Dung Chính
What Are Managed Apple IDs?
When Managed Apple IDs first became available, they were built for education and designed for IT administrators to use with Apple School Manager, and for students to use on Apple devices. They later became available to businesses (both for administrators and employees) with Apple Business Manager. The core functions for administrators remained the same: purchase app licenses for employees or devices using Apps and Books, manage and enroll devices into an MDM solution using Automated Device Enrollment, and manage roles and privileges of other Apple Business Manager users.
Managed Apple IDs made it easier to distribute apps and other content (specifically, books) more easily, as an alternative to having employees use their personal Apple IDs to acquire that content on their work devices. While it is possible for organizations to assign Apps and Book licenses to personal IDs using an MDM solution, it’s still difficult; users must agree to a series of prompts to make it possible. Company-owned and -managed IDs were meant to fix that.
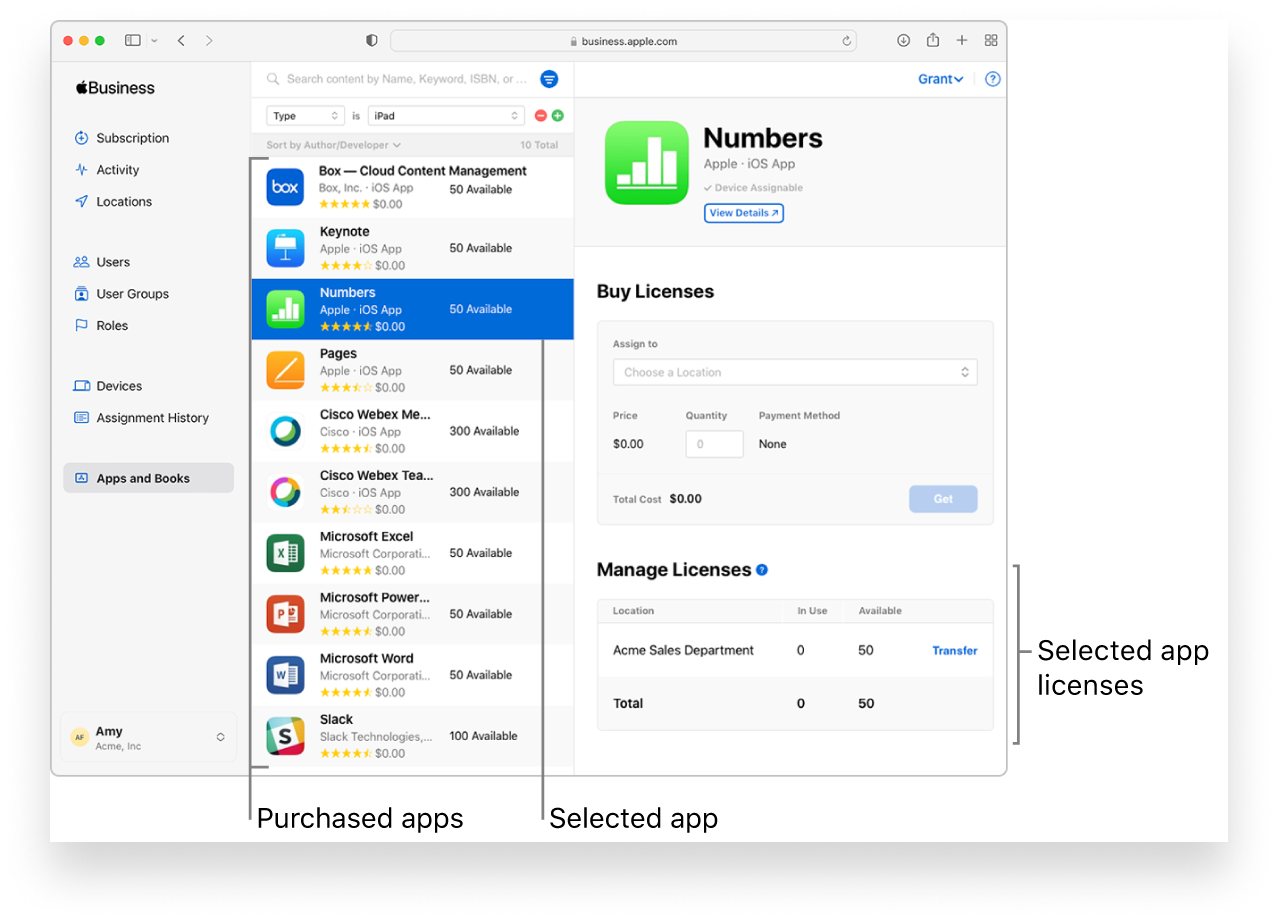
Image: apple.com
In reality, though, Managed Apple IDs aren’t used as much these days to distribute apps (which can be assigned directly to devices via MDM instead of to users) as they are to provide admin access to Apple Business Manager and to sign in to Shared iPad devices.
Pros and Cons of Using Managed Apple IDs
It’s easy to identify why Managed Apple IDs are beneficial to organizations. Such IDs:
- Are owned and managed by the organization;
- Can be created automatically, using federation with Microsoft Azure Active Directory (Azure AD) or Google Workspace;
- Can ensure that security policies enforced on the IdP side (including multifactor authentication) are automatically enforced;
- Enable individualized experiences on Shared iPad devices; and
- Ensure employees can’t create personal Apple IDs using organizationally-owned domains.
While there are no specific “cons” to using Managed Apple IDs, it’s important to note that for users or employees, they provide limited or no access to some Apple services: Some consumer features are simply turned off for Managed Apple IDs. (See Apple’s complete listing of those services).
How Do You Create a Managed Apple ID?
In years past, the only way for businesses to create Managed Apple IDs was to do so manually in Apple Business Manager. Today, while manual creation is still supported, Apple also supports integrating Apple Business Manager with both Azure AD and Google Workspace, which then enables the creation of Managed Apple IDs through federation.
Manually Creating Managed Apple IDs
The first method of creating Managed Apple IDs is in Apple Business Manager itself. For the details, see Apple’s support article on creating Managed Apple IDs in Apple Business Manager. Two important points to note: You’ll be required to choose one of the domains you’ve already registered (and verified) in Apple Business Manager. And you will need toassign a role to the new ID. You can always go back and edit details for a managed ID later.
Creating Managed Apple IDs through Federation
The second way to create Managed Apple IDs is by federating your organization’s Apple Business Manager account with Azure AD or Google Workspace. This method allows Managed Apple IDs to be automatically created just-in-time for identities that already appear in Azure AD or Google Workspace. Employees can then use their organizational credentials to sign in to Apple services; a Managed Apple ID will be provisioned for them on-demand. For more on how this federation works, see Apple’s documentation.
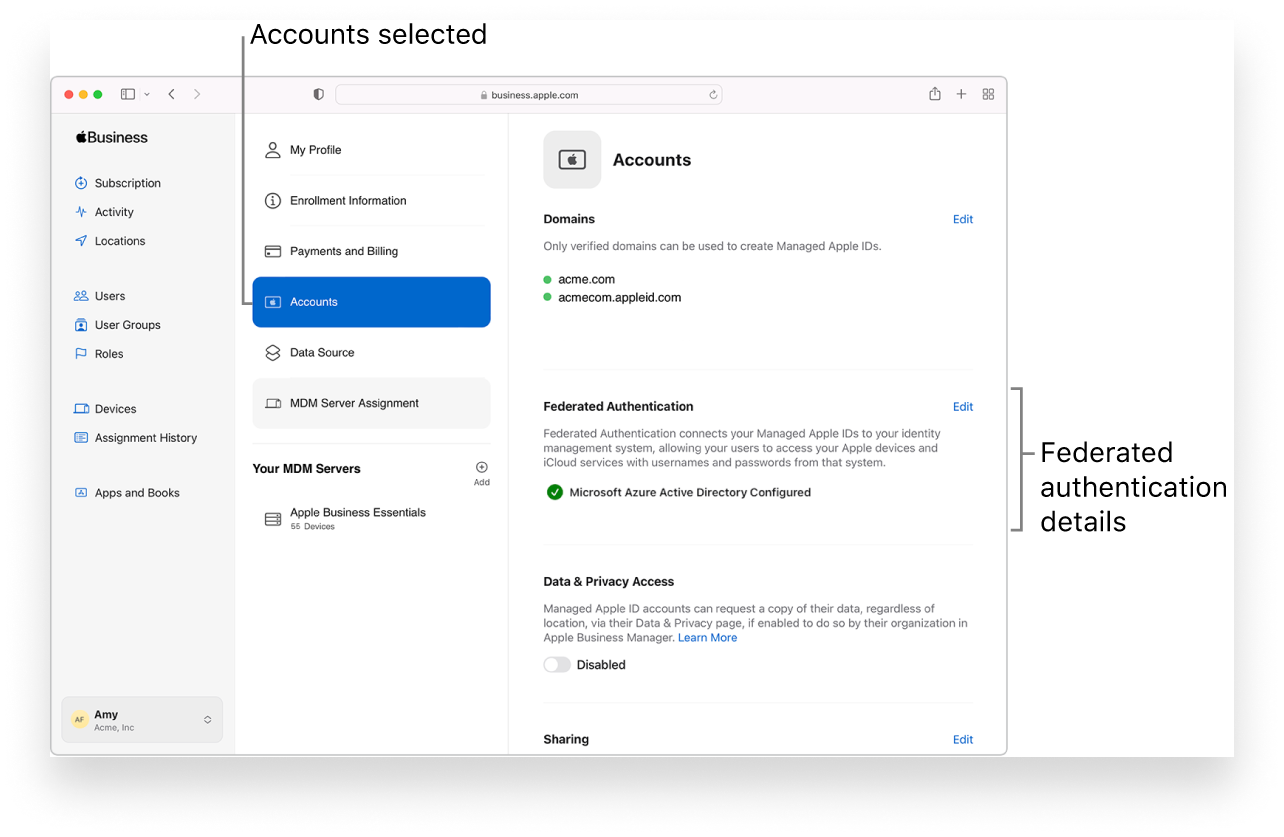
Image: Apple.com
Among the important points to know about federation: The domain you’re using must already be verified in Apple Business Manager. For Azure AD, each user’s User Principal Name (UPN) must match their email address, and it requires devices to be running macOS 10.13.4, iOS 11.3, and iPadOS 13.1 or later. Using Google Workspace requires iOS 15.5, iPadOS 15.5, or macOS 12.4 or later.
Syncing Users
In addition to federation, Apple also supports syncing user information from both Azure AD (using SCIM, or System for Cross-domain Identity Management) and Google Workspace to pre-create accounts for users. This can be helpful if it’s necessary to provision larger numbers of users with specific roles in Apple Business Manager, such as content managers to buy content in Apple and Books. For more information on syncing user data to Apple Business Manager, see Apple’s documentation for either Azure AD or Google Workspace.
How to Convert an Apple ID to a Managed Apple ID
When thinking about using Managed Apple IDs, one common question is, how do I convert existing Apple IDs to Managed Apple IDs?
While direct conversion isn’t possible, Apple has designed a conflict-resolution process that allows organizations to reclaim all domain namespace within the Apple ID system to the organization, while also allowing users who may have previously registered a work email address as a personal Apple ID to keep all of their existing purchased content.
The gist of that process: Apple notifies affected users both via email and natively on their devices to change the username of their Apple ID to something personal. For more information on the conflict resolution process and reclaiming domain namespace for Managed Apple IDs, see Apple’s documentation.
Remember, as noted previously, Managed Apple IDs are more restricted in the features and services they can access than regular consumer Apple IDs. So keeping work-use cases and personal ones separate are core to the design of Managed Apple IDs.
How to Use Managed Apple IDs for Business
There are two specific use cases for Managed Apple IDs that are worth calling out.
The first, as noted above, is to manage access and privileges for admins who play specific roles in Apple Business Manager.
Managed Apple IDs and Shared iPad
The second is Shared iPad, which allows multiple employees to use a single iPad while still enjoying the personalized experience of having one of their own.
Originally available only through Apple School Manager, Shared iPad was brought to business users in iPadOS 13.4. Before then, companies that wanted to share devices among their employees had to rely on custom workflows for resetting the devices between uses or third-party programs that worked with an MDM solution to quickly provision a device for a user. Now organizations can provide the same kind of user experience leveraging Managed Apple IDs.
When a user signs in to a shared iPad using a Managed Apple ID, iPadOS sets aside a section of the device’s storage space. Apple caches that user’s data (on the device itself, on local Content Caching devices, and in the cloud), so it can be retrieved when the user logs into another device. When the user logs out of the original device, their data is inaccessible to any other users and will not be recalled until the user enters their managed credentials again.
Shared iPad for business is supported on iPad mini (4th generation or later), iPad Air 2 (or later), iPad (5th generation or later), and all iPad Pro models. All devices must have at least 32 GB of storage.
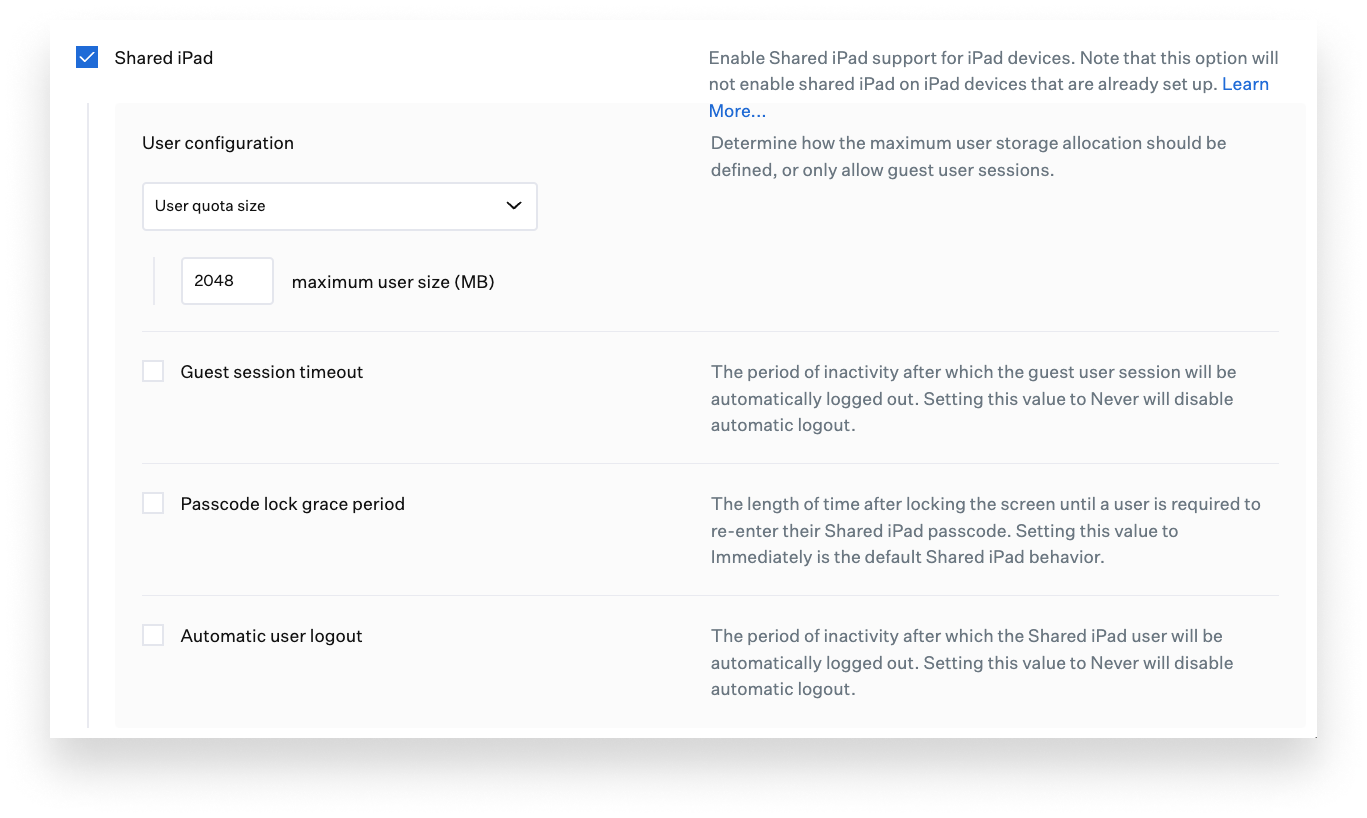
One important administrative detail to consider when making Shared iPad available: You have to decide how much of that storage to allocate for each user or (inversely) set a maximum number of users.
In Kandji, you can configure the maximum users or a per-user storage quota in the Automated Device Enrollment library item. That’s also where you enable temporary guest sessions, if you’d prefer that over—or in addition to—individualized experiences. It’s good to keep the number of users per device as low as possible and give them each as much storage as possible, to minimize iCloud communications and provide a faster sign-in experience.
It’s easiest to provide Shared iPad if you’ve federated your Apple Business Manager instance with Azure AD or Google Workspace. Users can then just use their regular credentials to sign in to a shared device. Otherwise, if you provision Managed Apple IDs from Apple Business Manager, you’ll have to create users one at a time in advance.
For this work, iPad devices to be shared must be enrolled via Automated Device Enrollment. Once enrolled, those devices will restart with Shared iPad enabled. The only way to remove a device from Shared iPad is to erase it.
While Shared iPad used to require the use of a Managed Apple ID, the temporary session feature introduced in iPadOS 13.4 allows multiple users to use a single device without authenticating. But when a temporary user logs out of that session on a Shared iPad, all data from it—including Safari browsing history, modified settings, and added files—are deleted.
While temporary sessions are convenient for many use cases, you need to be mindful of the networks those devices are connected to, to ensure network resources are protected appropriately. Allowing both Managed Apple IDs and temporary sessions, or just temporary sessions, is supported by Apple and can be configured in Kandji’s Automated Device Enrollment library item
Editor’s Note: This post was substantially revised from a previous version February 10, 2023.

Start your free trial today
The industry’s first MDM with a pre-built library of security controls.
Request Access






