How to Identify Apple Phishing Emails and Avoid Getting Scammed
Nội Dung Chính
Scams are getting more sophisticated. Learn what to look for so you don’t fall prey to an Apple phishing email.
It’s the end of a long day, and you open your email one last time. There, waiting at the top of your inbox, is a message from Apple asking you to confirm a purchase. The kids must have downloaded an app, you might think as you click on the link in the email to find out what they bought. Unfortunately, you may have just become the latest victim of an Apple phishing email.
What is phishing? It’s a type of scam in which fraudsters try to trick you into giving up personal information. Often, the scam arrives via an email, text message or phone call that appears to be from a legitimate company but really isn’t. If you click through using the link, you may soon find yourself googling “How to tell if my computer has been hacked” or wondering if your login credentials are on the most commonly used password list.
Even if they’re not, it’s easy to fall prey to phishing schemes, which have quickly become the most common type of internet-related crime. In 2021, the FBI’s Internet Crime Complaint Center received 323,972 complaints about phishing—a 34% increase over 2020. What’s worse, people who fell for these scams lost a total of more than $44 million. Read on to learn how to avoid online scams, then find out how to steer clear of Facebook Marketplace scams, Amazon scams and phone call scams.
What is phishing?
When hackers go phishing, they try to trick you into divulging personal information, such as passwords, bank information and Social Security numbers. They accomplish this by sending emails, texts (one of several types of texts you should immediately delete) and other types of messages that look like they’re coming from a legitimate company, like Amazon, your bank or your email provider.
These messages typically advise you of some problem with your account and ask you to click a link to remedy the situation. If you click, you may land on a website that looks like the real deal but is actually a form of spoofing. That website might ask you to enter your personal data, which bad actors then steal with ill intent. This type of scam is so common that one out of every 99 emails sent is a phishing email.
What is an Apple phishing scam?
In an Apple phishing scam, the fraudulent message appears to come from Apple, which is the second-most-impersonated brand (coming in just behind eBay). Sometimes the Apple phishing email looks like it’s from the App Store; other times, it may be associated with your Apple Pay account, your iTunes account or some other area of the Apple ecosystem.
One common type of Apple phishing email tries to get you to disclose your Apple ID and password, which you need to access Apple services like the App Store, Apple Music, iCloud, iMessage and FaceTime.
Why would someone phish for your Apple ID?
rd.com, Getty Images (2)
Your Apple ID account contains all your contact, payment and security information, which you can use to buy music, movies, apps, subscriptions and more.
If hackers discern your ID and password, they can dig even deeper, gaining private information, either for their own nefarious uses or to sell on the black market. “The bad guys get access to your iCloud email and the history of your app, music and movie purchases and rentals,” says Chris Hauk, consumer privacy champion at Pixel Privacy. They also have entree to all the documents, photos and files stored on your iCloud drive. They can even use your account to watch your movies and, in the latest scams, steal your money.
With more than 1.8 billion Apple devices currently in use, targeting Apple IDs can be a lucrative hustle for scammers.
How do Apple ID scams work?
Scammers have become very savvy and will use any method available to them to get your attention and try to phish for your information. Hauk says spoofed emails and texts are the most common methods. “They’re the easiest to pull off and don’t require any real programming skills on the part of the bad actor.”
But scammers will also target you through browser pop-up notices, phone calls and even calendar invitations. Usually, they try to entice you to click on a link or call a phone number for legitimate-sounding purposes but are actually trying to either steal, or get you to divulge, personal information. Often, scammers create a sense of urgency, says Russell Kent-Payne, director and co-founder of Certo Software, “so that their victims react quickly to the message and are then less likely to spot that it’s a fake.” They may even create a fake Apple virus warning.
What are the main Apple ID phishing scams to be aware of?
Hackers are continually inventing new scams and rehashing old ones. Some of the most common Apple ID phishing scams now include the following:
Apple support scam
rd.com, Getty Images
Running an Apple support scam is just one thing hackers can do if they have your phone number. Here’s how it works: You’ll receive a phone call—or often several calls in less than an hour—from what appears to be the real Apple support phone number. Instead, the number has been spoofed. If you answer the call, the scammer claims to be from Apple and says your Apple ID or iCloud account has been compromised. To fix things for you, they’ll say, they need your password or other sensitive information. Sometimes, rather than speaking with you directly, scammers will leave an automated voice message directing you to call a specific number for “Apple support.”
If you call the number, everything sounds legitimate, including updates telling you the anticipated hold time. When you finally connect with a human, they will ask you for compromising information. For the record, Apple will never call you to notify you of suspicious activity. In fact, Apple won’t call you for any reason—unless you request a call first. Phone scams like these are also known as vishing.
MetaMask Apple ID scam
This scam, which Kent-Payne says was discovered earlier this year, relies on the surging popularity of cryptocurrency and NFTs. In this case, scammers target MetaMask, a popular digital wallet for crypto, which is typically backed up to iCloud—a helpful security measure if your device is ever lost or stolen, Kent-Payne says.
This con usually starts once scammers know the email address associated with your Apple ID. They make multiple password reset requests, and you receive text alerts on your phone each time, sparking concern that your account may be comprised.
Next, says Kent-Payne, in a manner similar to the support scam, you receive a phone call that appears to come from Apple, warning you about suspicious activity on your account. Since this corresponds with the activity you’ve been seeing, it’s easy to believe the call is legitimate. With you on the line, the scammer requests another password reset, this time sending a six-digit verification code to your phone and then asking you for that code, all under the guise of verifying your identity.
Once they have that code, however, they are able to reset your Apple ID password. They can gain access to everything stored in iCloud, including your MetaMask wallet, and steal your cryptocurrency. One user lost $650,000 earlier this year as a result of this scam.
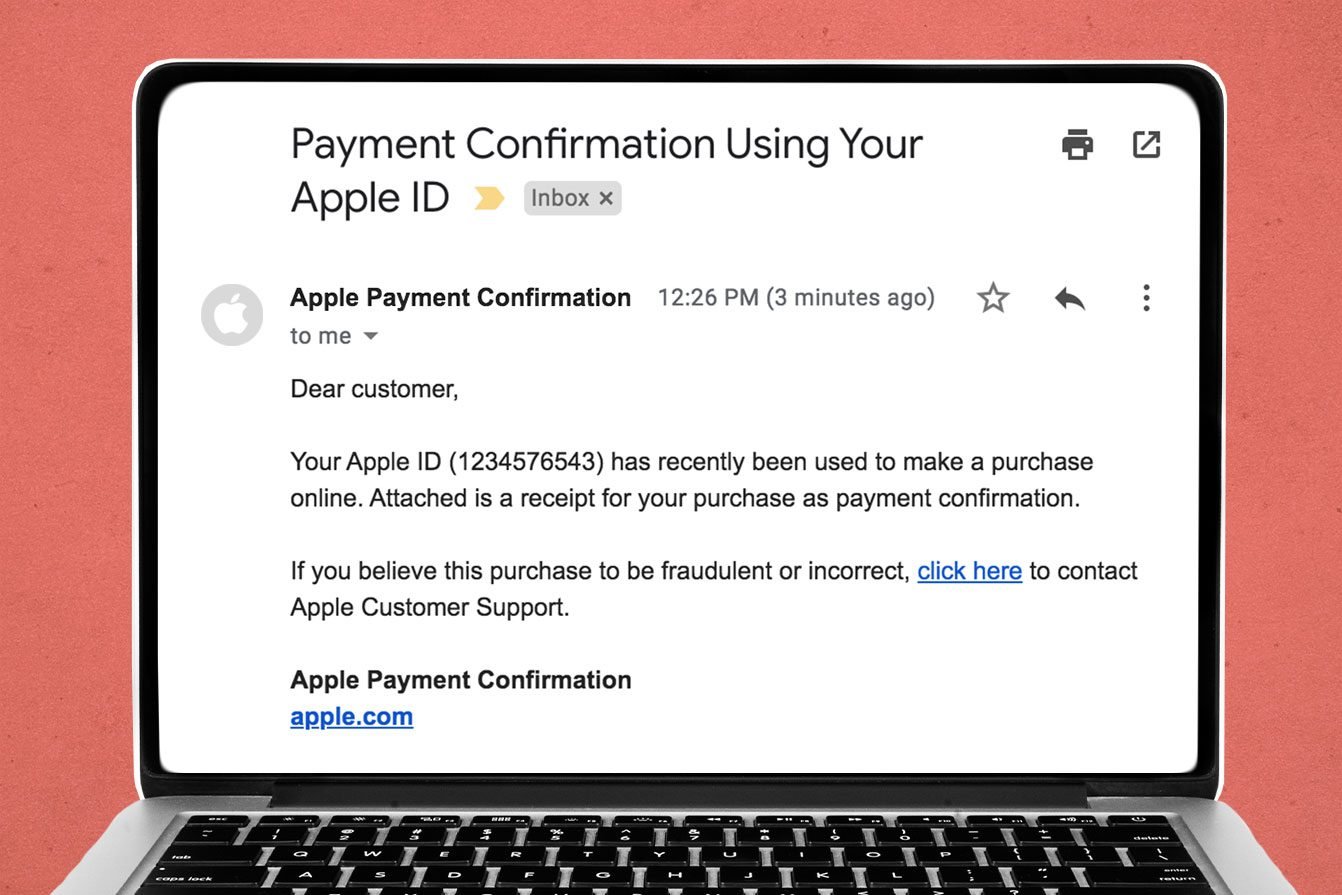
Apple ID order receipt
In this Apple phishing email scam, you’ll receive an email that appears to be from Apple, stating that your ID has been used to make a purchase, usually with a PDF receipt attached as “proof.” The email will either ask you to confirm the purchase or submit payment for it.
In either instance, you’ll typically see links that, if clicked, will take you to a fake Apple account management page. “It attempts to entice you to give up your Apple ID and password,” Hauk says.
Apple ID locked
This scam often works in tandem with the fake receipt scam. If you follow a spoofed email to a fake Apple page and then input your information, you may see a notification telling you that your account has been locked due to suspicious activity. It’ll then show you an “unlock” button, which requires you to divulge personally identifying information, such as your name, Social Security number, payment information and answers to common security questions.
Sometimes, this scam will arrive via an iMessage alert that states your Apple ID has been locked because your ID is about to expire. The message might ask you to complete a form to unlock your account. This, of course, gives the hackers access to sensitive info.
It’s true that Apple sometimes locks IDs if the company suspects fraudulent activity, but you can unlock your Apple ID by placing a phone call directly to Apple. It’s worth noting, however, that Apple IDs don’t expire, Kent-Payne says.
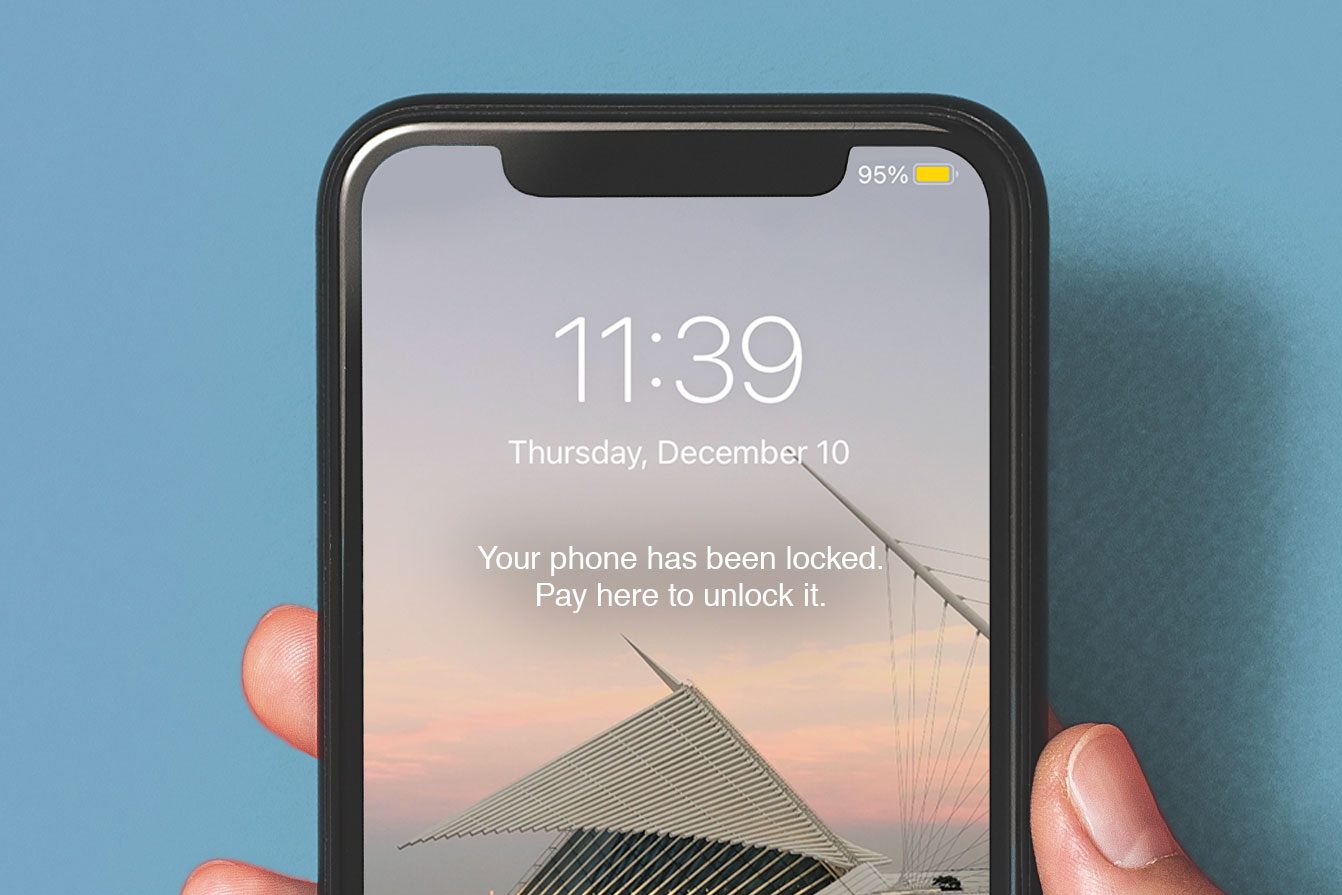
iPhone locked
If you get hit with a Find My iPhone scam, you’ve probably already fallen for at least one other Apple ID scam. If hackers have already gained access to your iCloud account, they could activate the Find My feature and place your device into “lost” mode, which remotely locks it. Then you’ll see a pop-up message on your phone saying that it will remain locked until you pay a ransom.
What are other types of Apple phishing scams?
Apple Pay suspended
In this scam, which Hauk says is becoming increasingly prevalent, people who use Apple Pay in their digital wallets may receive a text message on their phones warning that “Apple Pay has been suspended on your device.”
The message includes a link, which you can click to allegedly resolve the problem. If you tap the link, you land on a page that looks legitimate, with a message stating something like: “Apple Pay was suspended on your device. You can continue to make contactless purchases once you have reactivated your wallet.”
It’s easy to see why someone would click, but don’t! If you click through to the next page, it asks for personally identifying or financial information. Some users have had their identities stolen or their bank accounts emptied through this scam.
Apple gift card scam
Similar to the Apple support scam, the Apple gift card scam starts with a phone call. The person on the other end urgently insists that you need to make a payment of some kind—for a utility bill, taxes, hospital bill, debt collection, even bail money. They ask you to purchase an Apple Gift Card (sometimes with thousands of dollars loaded onto it) at your nearest electronics store, supermarket or convenience store and use it to pay the bill by sharing the code on the back of the card with them.
The catch: You can use Apple gift cards to purchase only goods and services from Apple—things like subscriptions to Apple Music, iCloud storage and products from Apple retail stores. If someone asks you to use it to pay for something else, it’s a sure bet they’re running a gift card scam, and the swindlers are using the number you just gave them to buy a sweet new phone or computer for themselves.
Calendar invitation
You might receive a spammy iCloud calendar invitation to a meeting or event from an unknown individual or group, often with promises for easy money, pornography or pharmaceuticals. You guessed it: If you click on a link or respond to the invitation in any way, you’re opening yourself up to phishing or, at the very least, more spam. Here’s how to stop iPhone calendar spam.
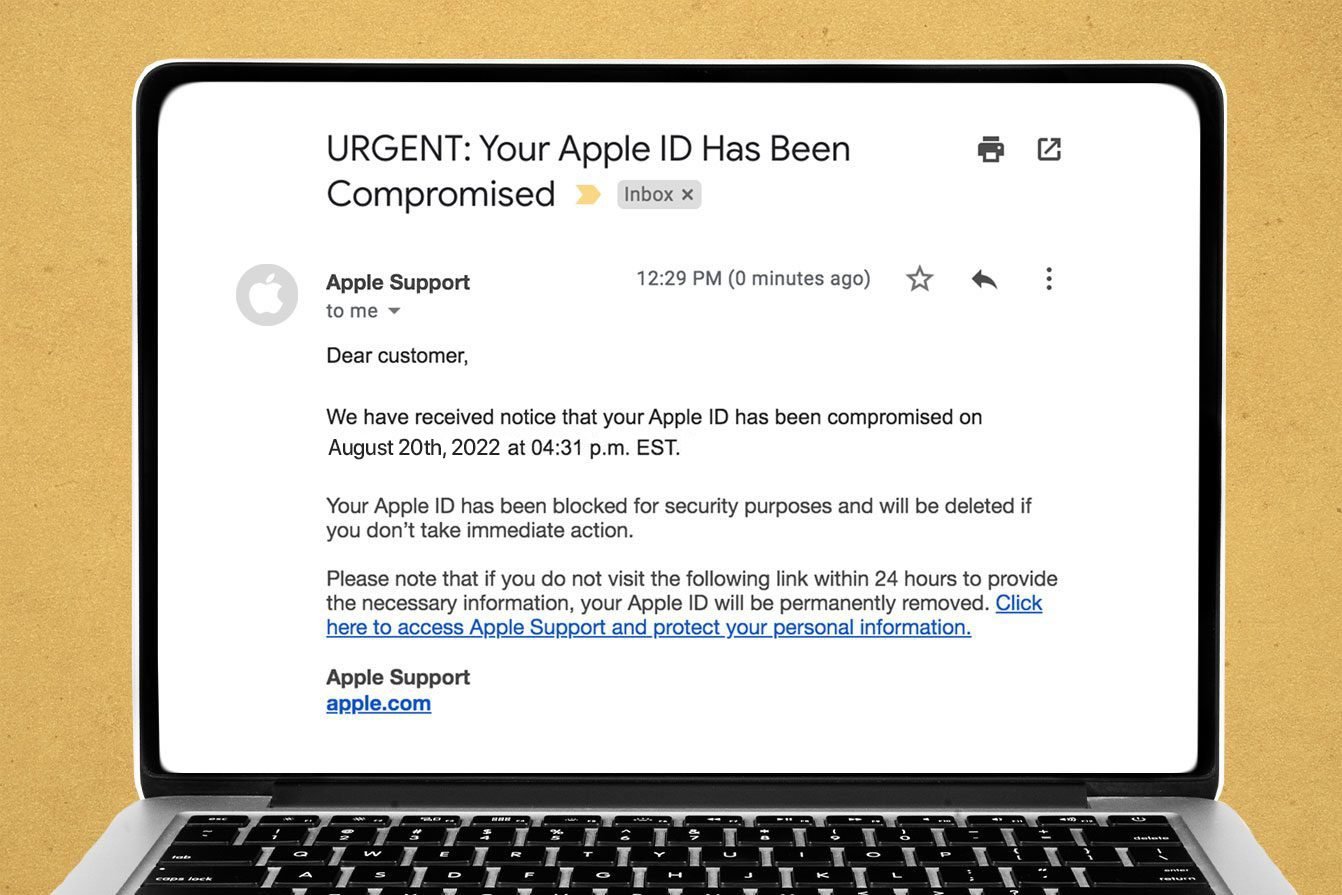
How to spot Apple ID phishing scams
 RD.com, Getty Images (2)
RD.com, Getty Images (2)
Scammers are becoming increasingly sophisticated in the art of making emails, texts and other communications look like the real deal. “Being able to recognize an attack is key to protecting yourself against phishing,” says Kent-Payne. Here’s what to look for.
- Spoofed address. Hover on the sender’s name in your inbox to see the full email address. If the message claims to be from Apple but the address is off by a letter or two—or worse, is just a bunch of random letters and numbers—it’s probably a phishing attempt.
- Suspicious links. Check the URL of any link sent in a text or email before clicking on it. “Scammers will often try to disguise the true destination of a link by changing its display address to something simple like ‘Click here’ or ‘Sign in,’” says Kent-Payne. “This makes it much harder for the victim to know they’re being taken to a malicious website.” On iOS devices, however, you can preview the true destination, he says. On an iPhone, just tap and hold the link, and a pop-up will appear, showing you the full URL. (On a Mac, hover your cursor over a link, and you’ll see the full URL at the bottom of the browser or in a pop-up in the email. “If the message claims to be from Apple but the link URL appears to have nothing to do with Apple, that’s a pretty good sign it is a scam.”
- Vague greeting. Reputable companies will usually address you by your full name, says Kent-Payne. Scammers will use something more generic, like “dear friend.”
- Misspellings, grammar mistakes and obvious typos. Reputable companies take pains to make sure their communication is clear, accurate and precise. Someone out to scam you may send a typo-ridden email.
- A sense of urgency. Phishing scams often create a false sense of urgency or rely on emotional manipulation to get you to act quickly.
Any legitimate email related to your Apple ID account will always come from [email protected] In addition, unlike Apple phishing emails, messages sent from Apple will never ask you to disclose your Apple ID password, Social Security number, your mother’s maiden name, your full credit card number or your credit or debit card’s CCV security code.
“Genuine purchase receipts—from purchases in the App Store, iTunes Store, iBooks Store or Apple Music—include your current billing address, which scammers are unlikely to have,” says Apple. You can also check your purchase history from any device without clicking on links in suspicious emails.
How to protect yourself from Apple ID phishing scams
The best way to avoid becoming the victim of a phishing attack is to never click on a link or attachment within an unsolicited email or text message, Hauk says.
The same holds true for phone calls. Apple and other companies will never call you out of the blue to discuss your device’s security. Don’t accept these calls or click on hyperlinked phone numbers within messages—and never answer a call from one of the suspicious area codes often used by scammers. If you have a concern about your device, visit Apple’s official website for information on whether your device or account truly has been compromised and what to do if it has. Don’t call the Apple number in your contacts if you think you’ve been scammed; a scammer’s spoofed number can appear there, as if it’s from Apple.
In addition to ignoring unsolicited communication, Kent-Payne suggests enabling two-factor authentication for any important accounts, including your Apple ID, email, social media and banking. “This means that even if a hacker works out your password via a phishing attack, they still can’t access your account,” he says.
He also recommends using Apple’s Message Filtering. That feature separates out any texts you receive from people who are not in your contacts and sends them to the “unknown senders” tab in your Messages list. You can turn on message filtering in Settings. (Go to “Messages” and toggle “Filter Unknown Senders” to the on position.) If you use filtering in conjunction with a good security app, such as Truecaller or SpamHound, the app can alert you when you receive a phishing message, Kent-Payne says.
And be sure to adhere to the following best practices:
- Never share your Apple ID password with anyone, including someone who says they’re from Apple.
- Keep your operating system updated to the latest version.
- Keep your browsers updated. Consider using a browser like Chrome, which has built-in phishing protections.
- Use antivirus and anti-malware programs on your devices.
- Always check the URL of any website into which you’ll be entering sensitive information. It should always start with “HTTPS” (the “s” stands for “secure”).
- Don’t reuse the same password on multiple sites. That just makes it easier for hackers. A password manager can help you keep track of strong, unique passwords.
What should you do if you receive an Apple ID phishing attempt?
rd.com, Getty Images
In most cases, you can safely close and ignore the email, text or pop-up, or hang up on the caller. Whatever you do, don’t click on any links or provide any personal information to the scammer. You should, however, report the attempt to the appropriate parties.
If you receive an Apple phishing email, forward it to [email protected] If you receive a suspicious iMessage or calendar invite, you should see an option under the message to “Report Junk.” If the option doesn’t appear, you can still block the sender. And if you get a fake tech-support phone call, you can report it to your local police department and to the Federal Trade Commission.
And if you happen to accidentally click on a suspicious link, don’t panic. “As long as you don’t supply any information that might be requested on a linked webpage, you should be OK,” Hauk says.
Did you already enter personal information? Immediately change your Apple ID password and enable two-factor authentication. Then review all the security information in your account to make sure it’s still accurate. You’ll want to check your name, your primary Apple ID email address and any other rescue emails or phone numbers, and your security questions and answers. Also check to see where your Apple ID is being used. You can find that information by going to Settings, then clicking on your name. If you see a device you don’t recognize, you can remove it from the list.
Sources:
- Chris Hauk, consumer privacy champion at Pixel Privacy
- Russell Kent-Payne, director and co-founder of Certo Software
- FBI: “Internet Crime Report 2021”
- Clario: “Startling Phishing Statistics to Be Aware of in 2022”
- Apple: “Recognize and avoid phishing messages, phony support calls, and other scams”
- Apple: “If you think your Apple ID has been compromised”
- Apple: “About Gift Card Scams”